This topic contains the following sections.
- Overview of AWS CloudTrail and Compliance Integration
- Overview of Deployment Scenarios
- Module Inputs Reference
- Module Dependencies
- Scenario 1 - Deploy New CloudTrail, and Add Configuration Assessment
- Scenario 2 - Integrate Existing CloudTrail and add Configuration Assessment
- Scenario 3 - Deploy New Consolidated CloudTrail and Configuration Assessment
- Scenario 4 - Integrate Existing Consolidated CloudTrail and Configuration Assessment
- Scenario 5 - AWS Organizations using AWS Control Tower
- Supplemental - For New or Existing CloudTrail with KMS Encrypted Buckets
- AWS security token service limitations
Lacework integrates with AWS to analyze CloudTrail for monitoring cloud account security, and for cloud resource configuration compliance. This document covers running Lacework Terraform Modules to integrate AWS with Lacework for both AWS CloudTrail and AWS Config using any host supported by Terraform.
If you are new to the Lacework Terraform Provider, or Lacework Terraform Modules, be sure to read through the Terraform for Lacework Overview article to learn the basics on how to configure the provider, and more.
Overview of AWS CloudTrail and Compliance Integration
To integrate AWS with Lacework, Lacework Terraform Modules will provision the following resources in the designated AWS account:
- IAM Cross Account Role - A cross account role is required to give access to Lacework access for assessments of cloud resource configurations and for analysis of CloudTrail events. The cross account role will be given the following policies:
- SecurityAudit - AWS Managed Policy to provide read-only access to cloud resource configurations.
- Lacework Custom Audit Policy - A custom policy that extends SecurityAudit to enable read-only access to additional configuration resources.
- Lacework Custom IAM Policy - A custom policy that provides Lacework read-only access to ingest CloudTrail logs.
- CloudTrail - Lacework can create a new trail or use an existing CloudTrail.
- S3 Bucket - An S3 bucket is required for all CloudTrail integrations. Lacework can use an existing bucket or create a new bucket in the designated account.
- SNS Topic - An SNS topic is required for all CloudTrail integrations. Terraform can use an existing SNS topic or create one if an SNS topic has not be added to an existing CloudTrail.
- SQS Queue - An SQS queue is required for all CloudTrail integrations and monitored by Lacework.
Requirements
- AWS Account Admin - The account used to run Terraform must have administrative privileges on every AWS account you intend to integrate with Lacework.
- AWS CLI - The Terraform Provider for AWS leverages the configuration from the AWS CLI and it is recommended the AWS CLI is installed and configured with API Keys for the account being integrated.
- Lacework Administrator - You must have a Lacework account with administrator privileges.
- Terraform -
>= 0.12.31,~> 0.13,~> 0.14,~> 0.15,~> 1.0.
Overview of Deployment Scenarios
Lacework’s Terraform Modules for AWS support the following deployment scenarios:
- Deploy New CloudTrail and Add Configuration Assessment - This deployment scenario will configure a new CloudTrail in an AWS account, Configure an AWS account for cloud resource configuration assessment, and integrate the AWS account with Lacework.
- Integrate Existing CloudTrail and add Configuration Assessment - This deployment scenario uses an existing CloudTrail, S3 bucket, and can create a new or use an existing SNS topic passed as inputs to the module. The example creates the SQS queue and IAM Role for Lacework, and then configures both integrations with Lacework.
- New Consolidated CloudTrail - This scenario enables a new Consolidated CloudTrail and IAM Role for Lacework, then configures both integrations with Lacework. Finally, it configures a new CloudTrail Trail in an AWS sub-account that points to the main CloudTrail.
- Existing Consolidated CloudTrail - This scenario uses an Consolidated CloudTrail and creates an IAM Role for Lacework, then configures all sub accounts to be integrated with Lacework.
- AWS Organization using Control Tower or similar structure - This scenario is for integrating with AWS Organizations that use AWS Control Tower (or similar setup) to automatically set up their CloudTrail logging. This scenario uses a different module that only creates an IAM Role for Lacework in the
log_archiveaccount and an SQS queue in theauditaccount. - Supplemental: New or Existing CloudTrail with KMS Bucket Encryption - Additional parameters for use of KMS-encyrpted S3 buckets.
Module Inputs Reference
For an up-to-date guide on all available configuration inputs, please refer to the documentation on the Terraform Registry:
- AWS CloudTrail Module Inputs
- AWS Config Module Inputs
- AWS IAM Role Module Inputs
- AWS CloudTrail for Control Tower Module Inputs
Module Dependencies
Lacework Terraform modules for AWS have the following dependencies that will be installed when running terraform init:
For detailed information on these dependencies, visit Lacework on the Terraform Registry.
Scenario 1 - Deploy New CloudTrail, and Add Configuration Assessment
In this scenario a new CloudTrail will be created in an AWS account along with a cross-account IAM role to provide Lacework access to monitor CloudTrail, AWS resource configurations, and integrate the AWS account into Lacework.
terraform {
required_providers {
lacework = {
source = "lacework/lacework"
version = "~> 0.3"
}
}
}
provider "aws" {
region = "YourAWSRegion"
}
provider "lacework" {}
module "aws_config" {
source = "lacework/config/aws"
version = "~> 0.1"
}
module "aws_cloudtrail" {
source = "lacework/cloudtrail/aws"
version = "~> 0.1"
bucket_force_destroy = true
use_existing_iam_role = true
iam_role_name = module.aws_config.iam_role_name
iam_role_arn = module.aws_config.iam_role_arn
iam_role_external_id = module.aws_config.external_id
}
- Ensure you have have the Lacework CLI installed and configured to the Lacework account you plan to integrate.
- Open an editor of your choice (VSCode, Atom, or VIM) and create a new file called
main.tf. - Copy the code snippet above and paste it into the
main.tffile. - Open a Terminal and change directories to the directory that contains the
main.tffile and runterraform initto initialize the project and download the required modules. - Run
terraform planto validate the configuration and review pending changes. - After you review the pending changes, run
terraform applyto execute changes.
Note: Lacework Terraform modules provide a number of inputs for customization. Visit the documentation on the Terraform Registry for the complete list of inputs for each module.
Validate The Configuration
Once Terraform finishes applying changes, use the Lacework CLI or log in to the Lacework Console to confirm the integration is working.
For the CLI open a Terminal and run the command lacework integrations list (The integrations will be listed as AWS_CFG and AWS_CT_SQS).
To validate the integration via the Lacework Console, log in to your account and go to Settings > Integrations > Cloud Accounts.
Scenario 2 - Integrate Existing CloudTrail and add Configuration Assessment
In this scenario Terraform configures a cross-account IAM role to provide Lacework access to monitor an existing CloudTrail. That same cross-account role also provides Lacework permissions to audit AWS resource configurations and integrate the AWS account into Lacework. An SQS queue will be created for Lacework, and optionally you can deploy an SNS topic for that SQS queue if one does not already exist.
About SNS Topics
AWS CloudTrail provides an option to create an SNS topic, which is required to integrate AWS environments with Lacework. Lacework's Terraform Module for CloudTrail by default will create a new SNS topic. The SNS topic must be created in the same region as the existing CloudTrail, and it must be manually attached to the CloudTrail by logging in to the AWS console, navigating to CloudTrail, and then selecting the new SNS topic.
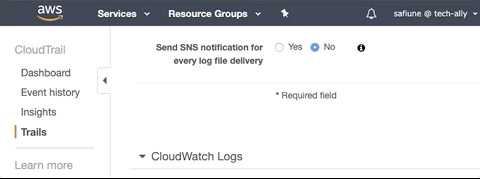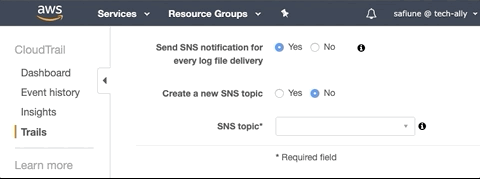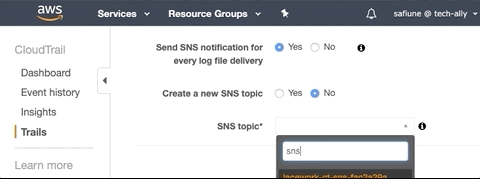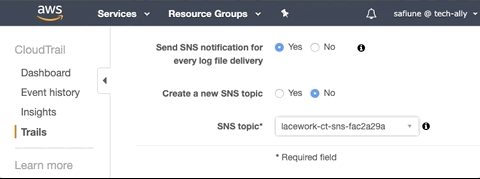
Additionally, if you have an SNS topic configured on the existing CloudTrail that you want to use with Lacework, specify it using the input sns_topic_name = "YourSNSTopicName".
terraform {
required_providers {
lacework = {
source = "lacework/lacework"
version = "~> 0.3"
}
}
}
provider "aws" {
region = "YourRegionOfExistingCloudTrail"
}
provider "lacework" {}
module "aws_config" {
source = "lacework/config/aws"
version = "~> 0.1"
}
module "aws_cloudtrail" {
source = "lacework/cloudtrail/aws"
version = "~> 0.1"
use_existing_cloudtrail = true
bucket_arn = "YourExistingBucketARN"
bucket_name = "YourExistingBucketName"
use_existing_iam_role = true
iam_role_name = module.aws_config.iam_role_name
iam_role_arn = module.aws_config.iam_role_arn
iam_role_external_id = module.aws_config.external_id
}
Note: Terraform must be configured to run using the account that owns the S3 bucket used with the cloudtrail.
- Ensure you have have the Lacework CLI installed and configured to the Lacework account you plan to integrate.
- Open an editor of your choice (VSCode, Atom, or VIM) and create a new file called
main.tf. - Copy the code snippet above and paste it into the
main.tffile. - Update the
region,bucket_arn, andbucket_name. - If you have an SNS topic configured on the existing CloudTrail, specify it using the input
sns_topic_name = "YourSNSTopicName". If you do not have an existing SNS Topic configured on the existing CloudTrail, the Terraform module will automatically create one, but you must manually attach the SNS Topic to the existing CloudTrail. - Open a Terminal and change directories to the directory that contains the
main.tffile and runterraform initto initialize the project and download the required modules. - Run
terraform planto validate the configuration and review pending changes. - After you review the pending changes, run
terraform applyto execute changes.
Note: Lacework Terraform modules provide a number of inputs for customization. Visit the documentation on the Terraform Registry for the complete list of inputs for each module.
Validate The Configuration
Once Terraform finishes applying changes, use the Lacework CLI or log in to the Lacework Console to confirm the integration is working.
For the CLI open a Terminal and run the command lacework integrations list (The integrations will be listed as AWS_CFG and AWS_CT_SQS).
To validate the integration via the Lacework Console, log in to your account and go to Settings > Integrations > Cloud Accounts.
Scenario 3 - Deploy New Consolidated CloudTrail and Configuration Assessment
Lacework supports the integration of consolidated CloudTrail deployments where multiple sub accounts send CloudTrail logs to a main CloudTrail account.
This scenario enables an organization CloudTrail and a cross-account IAM role to give Lacework access to CloudTrail and integrates the AWS accounts into Lacework.
terraform {
required_providers {
lacework = {
source = "lacework/lacework"
version = "~> 0.3"
}
}
}
provider "lacework" {}
provider "aws" {
alias = "main"
region = "YourAWSRegion"
profile = "[profile name for the main account in ~/.aws/credentials]"
}
module "aws_config_main" {
source = "lacework/config/aws"
version = "~> 0.1"
providers = {
aws = aws.main
}
}
module "main_cloudtrail" {
source = "lacework/cloudtrail/aws"
version = "~> 0.1"
providers = {
aws = aws.main
}
consolidated_trail = true
use_existing_iam_role = true
iam_role_name = module.aws_config_main.iam_role_name
iam_role_arn = module.aws_config_main.iam_role_arn
iam_role_external_id = module.aws_config_main.external_id
}
provider "aws" {
alias = "sub_account"
region = "YourAWSRegion"
profile = "[profile name for the sub account in ~/.aws/credentials]"
}
module "aws_config_sub_account" {
source = "lacework/config/aws"
version = "~> 0.1"
providers = {
aws = aws.sub_account
}
}
resource "aws_cloudtrail" "lw_sub_account_cloudtrail" {
provider = aws.sub_account
name = "lacework-sub-trail"
is_multi_region_trail = true
s3_bucket_name = module.main_cloudtrail.bucket_name
sns_topic_name = module.main_cloudtrail.sns_arn
}
For more information on organization level CloudTrail deployments visit AWS documentation site
- Ensure you have have the Lacework CLI installed and configured to the Lacework account you plan to integrate.
- Open an editor of your choice (VSCode, Atom, or VIM) and create a new file called
main.tf. - Copy the code snippet above and paste it into the
main.tffile. - Open a Terminal and change directories to the directory that contains the
main.tffile and runterraform initto initialize the project and download the required modules. - Run
terraform planto validate the configuration and review pending changes. - After you review the pending changes, run
terraform applyto execute changes.
Note: Lacework Terraform modules provide a number of inputs for customization. Visit the documentation on the Terraform Registry for the complete list of inputs for each module.
Validate The Configuration
Once Terraform finishes applying changes, use the Lacework CLI or log in to the Lacework Console to confirm the integration is working.
For the CLI open a Terminal and run the command lacework integrations list (The integrations will be listed as AWS_CFG and AWS_CT_SQS).
To validate the integration via the Lacework Console, log in to your account and go to Settings > Integrations > Cloud Accounts.
Scenario 4 - Integrate Existing Consolidated CloudTrail and Configuration Assessment
Lacework supports the integration of consolidated CloudTrail deployments where multiple sub accounts send CloudTrail logs to a main CloudTrail account.
This scenario uses an existing consolidated CloudTrail, and deploys a cross-account IAM role to give Lacework access to CloudTrail and integrates the AWS accounts into Lacework. The cross account role also provides Lacework access to assess cloud resource configurations.
terraform {
required_providers {
lacework = {
source = "lacework/lacework"
version = "~> 0.3"
}
}
}
provider "lacework" {}
provider "aws" {
alias = "main"
region = "YourAWSRegion"
profile = "[profile name for the main account in ~/.aws/credentials]"
}
module "aws_config_main" {
source = "lacework/config/aws"
version = "~> 0.1"
providers = {
aws = aws.main
}
}
module "main_cloudtrail" {
source = "lacework/cloudtrail/aws"
version = "~> 0.1"
providers = {
aws = aws.main
}
consolidated_trail = true
use_existing_cloudtrail = true
bucket_arn = "YourExistingBucketARN"
bucket_name = "YourExistingBucketName"
}
provider "aws" {
alias = "sub_account"
region = "YourAWSRegion"
profile = "[profile name for the sub account in ~/.aws/credentials]"
}
module "aws_config_sub_account" {
source = "lacework/config/aws"
version = "~> 0.1"
providers = {
aws = aws.sub_account
}
}
For more information on organization level CloudTrail deployments visit AWS documentation site.
- Ensure you have the Lacework CLI installed and configured to the Lacework account you plan to integrate.
- Open an editor of your choice (VSCode, Atom, or VIM) and create a new file called
main.tf. - Copy the code snippet above and paste it into the
main.tffile. - Update the
region,bucket_arn, andbucket_name. - If you have an SNS topic configured on the existing CloudTrail, specify it using the input
sns_topic_name = "YourSNSTopicName". If you do not have an existing SNS Topic configured on the existing CloudTrail, the Terraform module will automatically create one, but you must manually attach the SNS Topic to the existing CloudTrail. - Open a Terminal and change directories to the directory that contains the
main.tffile and runterraform initto initialize the project and download the required modules. - Run
terraform planto validate the configuration and review pending changes. - After you review the pending changes, run
terraform applyto execute changes.
Note: Lacework Terraform modules provide a number of inputs for customization. Visit the documentation on the Terraform Registry for the complete list of inputs for each module.
Validate The Configuration
Once Terraform finishes applying changes, use the Lacework CLI or log in to the Lacework Console to confirm the integration is working.
For the CLI open a Terminal and run the command lacework integrations list (The integrations will be listed as AWS_CFG and AWS_CT_SQS).
To validate the integration via the Lacework Console, log in to your account and go to Settings > Integrations > Cloud Accounts.
Scenario 5 - AWS Organizations using AWS Control Tower
Lacework supports the integration of consolidated CloudTrail for AWS Organizations using AWS Control Tower (or similar deployments) that split up the S3 bucket for the consolidated CloudTrail and the subscribed SNS topic.
This scenario uses an existing consolidated CloudTrail in an S3 bucket, deploys a cross-account IAM role to the log_archive account to give Lacework access to that S3 bucket, deploys an SQS queue for the existing SNS topic in the audit account and finally, integrates the AWS accounts into Lacework.
terraform {
required_providers {
lacework = {
source = "lacework/lacework"
version = "~> 0.3"
}
}
}
provider "lacework" {}
provider "aws" {
alias = "log_archive_account"
region = "YourAWSRegion"
profile = "[profile name for log_archive account in ~/.aws/credentials]"
}
provider "aws" {
alias = "audit_account"
region = "YourAWSRegion"
profile = "[profile name for audit account in ~/.aws/credentials]"
}
module "cloudtrail-controltower" {
source = "lacework/cloudtrail-controltower/aws"
version = "~> 0.1"
providers = {
aws.audit = aws.audit_account
aws.log_archive = aws.log_archive_account
}
# The only two required variables are the SNS topic ARN and the S3 Bucket ARN where the CloudTrail logs are stored
# SNS Topic ARN is usually in the form: arn:aws:sns:[control_tower_region]:[aws_audit_account_id]:aws-controltower-AllConfigNotifications
sns_topic_arn = "arn:aws:sns:[control_tower_region]:[aws_audit_account_id]:aws-controltower-AllConfigNotifications"
# S3 Bucket ARN is usually in the form: arn:aws:s3:::aws-controltower-logs-[log_archive_account_id]-[control_tower_region]
s3_bucket_arn = "arn:aws:s3:::aws-controltower-logs-[log_archive_account_id]-[control_tower_region]"
}
For more information on organization level CloudTrail deployments visit AWS documentation site. For more information on AWS Organizations, visit AWS documentation site For more information on AWS Control Tower, visit AWS documentation site
- Ensure you have the Lacework CLI installed and configured to the Lacework account you plan to integrate.
- Ensure you have your multiple account credentials in your ~/.aws/credentials file.
- Open an editor of your choice (VSCode, Atom, or VIM) and create a new file called
main.tf. - Copy the code snippet above and paste it into the
main.tffile. - Update the AWS provider
profile,region,sns_topic_arn, ands3_bucket_arn. - (Optional) If you have an IAM role in your
log_archiveaccount that you would like to use, first setuse_existing_iam_role = true, then specify the account using the inputiam_role_nameandiam_role_arn. If you do not have an existing IAM role configured in yourlog_archiveaccount, the Terraform module will automatically create one. This IAM role MUST be in thelog_archiveaccount, not theauditaccount. - Open a Terminal and change directories to the directory that contains the
main.tffile and runterraform initto initialize the project and download the required modules. - Run
terraform planto validate the configuration and review pending changes. - After you review the pending changes, run
terraform applyto execute changes.
Note: Lacework Terraform modules provide a number of inputs for customization. Visit the documentation on the Terraform Registry for the complete list of inputs for each module.
Validate The Configuration
Once Terraform finishes applying changes, use the Lacework CLI or log in to the Lacework Console to confirm the integration is working.
For the CLI open a Terminal and run the command lacework integrations list (The integrations will be listed as AWS_CFG and AWS_CT_SQS).
To validate the integration via the Lacework Console, log in to your account and go to Settings > Integrations > Cloud Accounts.
Supplemental - For New or Existing CloudTrail with KMS Encrypted Buckets
Lacework supports reading from KMS-encrypted CloudTrail buckets by configuring the cross-account role to give Lacework access to the KMS key.
When the below inputs are added to your terraform plan, your CloudTrail and S3 will be configured to use the provided KMS key, and your cross-account role will be updated to allow Lacework to read the KMS key.
| Input | Details |
|---|---|
| bucket_enable_encryption | Set this to true |
| bucket_sse_algorithm | For KMS, specify aws:kms |
| bucket_sse_key_arn | Specify the ARN of your KMS key. (Access to this key will be granted to the Lacework IAM cross-account role.) |
Example
module "aws_cloudtrail" {
source = "lacework/cloudtrail/aws"
version = "~> 0.1"
... More code here ...
bucket_enable_encryption = true
bucket_sse_algorithm = "aws:kms"
bucket_sse_key_arn = "arn:aws:kms:example-region-1:123456789098:key/111aa2bb-333c-4d44-5555-a111bb2c33dd"
}
AWS security token service limitations
The Lacework AWS module will fail due to limitations of STS. See AWS STS documentation for more information.
Customers using aws-vault for example will need to pass the --no-session flag. More information can be found on aws-vault documentation.
