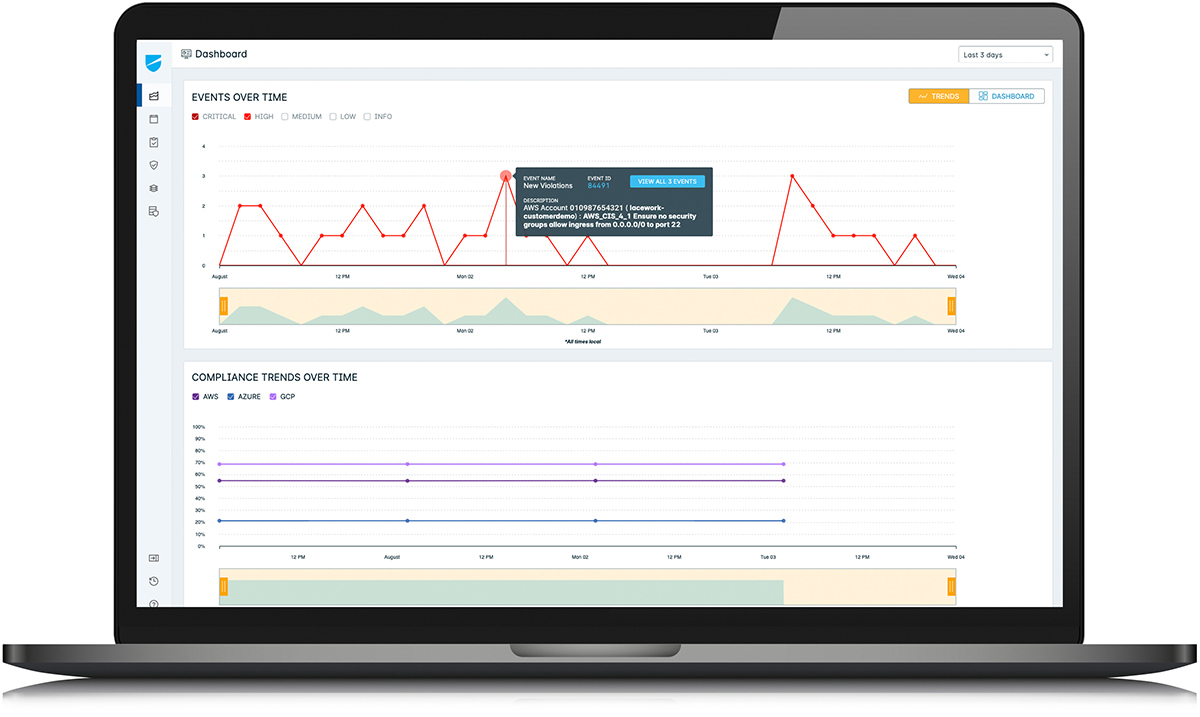
Lacework offers comprehensive cloud account security for AWS, Azure, and GCP accounts that provides insights about configuration changes that could lead to threats. At the console level of a cloud environment, an organization can inadvertently apply misconfigurations that could leak data or open up an easy attack surface to a hacker. With continuous updates and broad administrative access happening within cloud environments, account changes are normal. Yet with increased activity comes increased vulnerability.
Through API integration between accounts, Lacework looks at all of the security-relevant configurations and identifies where the organization is passing or failing certain account security best practices for these particular configurations. These checks are run continuously, and security teams receive automated alerts about any configuration changes that violate security compliance. Among a myriad of issues, it is able to identify things such as:
- S3 buckets in AWS that are misconfigured and left publicly open
- Security groups allowing unrestricted access to SSH
- IAM users that don’t have MFA enabled
- Security groups that are misconfigured
- New regions are being spun up specifically for Bitcoin mining
Data from the cloud accounts is ingested, and Lacework applies machine learning to logs to generate high fidelity alerts on any behaviors or events that could be an indicator of compromise at the account resource level. Lacework also proactively alerts on any account security misconfigurations at the time they occur.
Monitor Ongoing Activity
- Detects and alerts of activity on all cloud platform resources, such as new activity in a region, activation of new services, or changes to access control lists
- Notes changes to cloud account users, roles, or access policies
- Prevents access or customer master key tampering
- Reduces alert fatigue with customizable alerts and reports that eliminate repetitive or irrelevant results
Identify Configuration Issues
- Find Identity and Access Management (IAM) vulnerabilities, including root account, password requirements, and MFA usage
- Check for logging best practices, enable log files across regions, and ensure that log files are validated and encrypted
- Monitor critical account activity such as unauthorized API calls and use of the management console for unauthorized purposes
- Confirm secure network configurations
Track Configuration Continuously
- Maintain compliance and protection with a daily re-audit
- Monitor account activity for abnormal activity, even when that activity is technically authorized
- Receive customizable alerts when items change from compliant to non-compliant