Don’t let security put your data at risk
Agentless side scanning exfiltrates data from your environment for analysis. Lacework uses least privilege and keeps your data within your control.
See the difference
Point solutions can only get you so far
Features
Lacework
Wiz
Cloud native application protection platform (CNAPP)
Security through the entire app development lifecycle

Full visibility from build time through runtime

Partial runtime coverage (K8s workloads only)
Cloud security posture management (CSPM)
Uncover misconfigurations and compliance risks


Infrastructure as Code (IaC) security
Address risk at the earliest stage possible


Cloud workload protection platform (CWPP)
Protect workloads continuously with runtime threat detection

Continuously monitor for known and unknown threats in workloads

Sensor only supports K8s workloads
Workload scanning that’s secure by default
Safely find and prioritize vulnerabilities within your own unique environment

Carefully architected platform to ensure your data is secure by default

Product requires permission to snapshot and copy your data into their cloud account for scanning
A mature, optimized, time-proven agent
Have full visibility into cloud runtime activity

Time-proven agent supports nearly 20 different environments

No continuous runtime visibility
Audit log analysis, without painful rules
Monitor user and resource activity through cloud audit logs

Analyzes and correlates cloud audit logs to uncover issues, no manual rules required

Audit log ingestion, also referred to as Cloud Detection and Response (CDR), requires rules and signatures
Behavior-based threat detection
Find all suspicious behavior in your cloud, uncovering zero day threats

Pinpoints deviations from your unique environment’s baseline in near real-time

Requires rules, which lead to noise
Custom vulnerability scoring
Reduce vulnerability noise with a custom risk score


Gaps in runtime visibility and does not prioritize based on a unique cloud environment
Cloud Infrastructure Entitlement Management (CIEM)
Prioritize identity risks, while detecting identity-based attacks

Lacework surfaces your riskiest cloud identities, while using anomaly detection to pinpoint identity-based threats

Wiz focuses on identity risk but lacks identity threat capabilities
3 reasons why customers choose Lacework over Wiz
Private by design and by default
Wiz sends snapshots out of a customer environment for analysis, expanding the attack surface. Lacework agentless workload scanning is private by design and by default and doesn’t exfiltrate your data.
A partner that scales alongside you
Although Wiz is a simple solution for identifying risk, the data-driven Lacework platform is designed to support customers for the long term as they mature their cloud security practice.
Out with point solutions. In with data-driven platforms
With a single, comprehensive CNAPP solution, Lacework delivers security from code to cloud — no rule-writing required. Teams can finally reach operational nirvana.
Recognized Leader in Cloud and Workload Security

G2 CROWD LEADER
Cloud Security

G2 CROWD LEADER
Cloud Security Monitoring and Monitoring

G2 CROWD LEADER
Cloud Compliance

G2 CROWD LEADER
Container Security

G2 CROWD LEADER
CWPP

G2 CROWD LEADER
CSPM

G2 CROWD LEADER
CNAPP

G2 CROWD ENTERPRISE LEADER
Cloud Security
Make everything you build cloud secure
Stop costly mistakes at the source
Fix vulnerabilities and misconfigurations before they hit production. Add security checks early in development, including infrastructure as code (IaC) scanning. Empower developers to scan locally, in registries, and CI/CD while building, at scale.
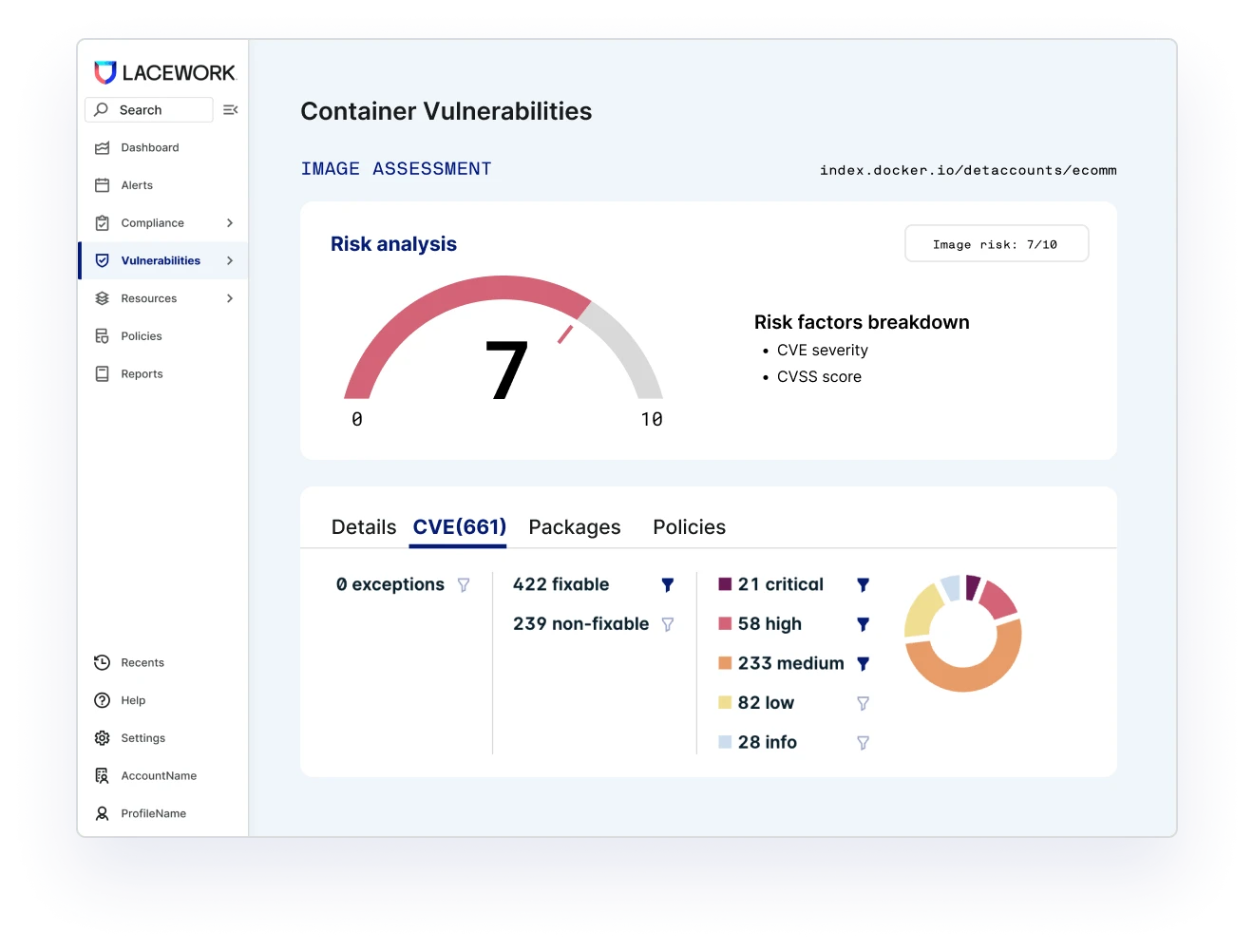
Prioritize your most exploitable risks
Tie together risk factors — vulnerabilities, misconfigurations, network reachability, secrets, and more — to see how attackers can compromise your cloud. Automatically connect with insights into what’s happening in runtime to prioritize critical risks, investigate faster, and even see suggestions for remediation.
Know your cloud and its weak spots
Deploy agentlessly to understand cloud risks in minutes. Get instant visibility into what’s deployed, how it’s configured, and pinpoint vulnerabilities and misconfigurations. We scan everything – workloads, container images, hosts, and language libraries – so no secret can hide.
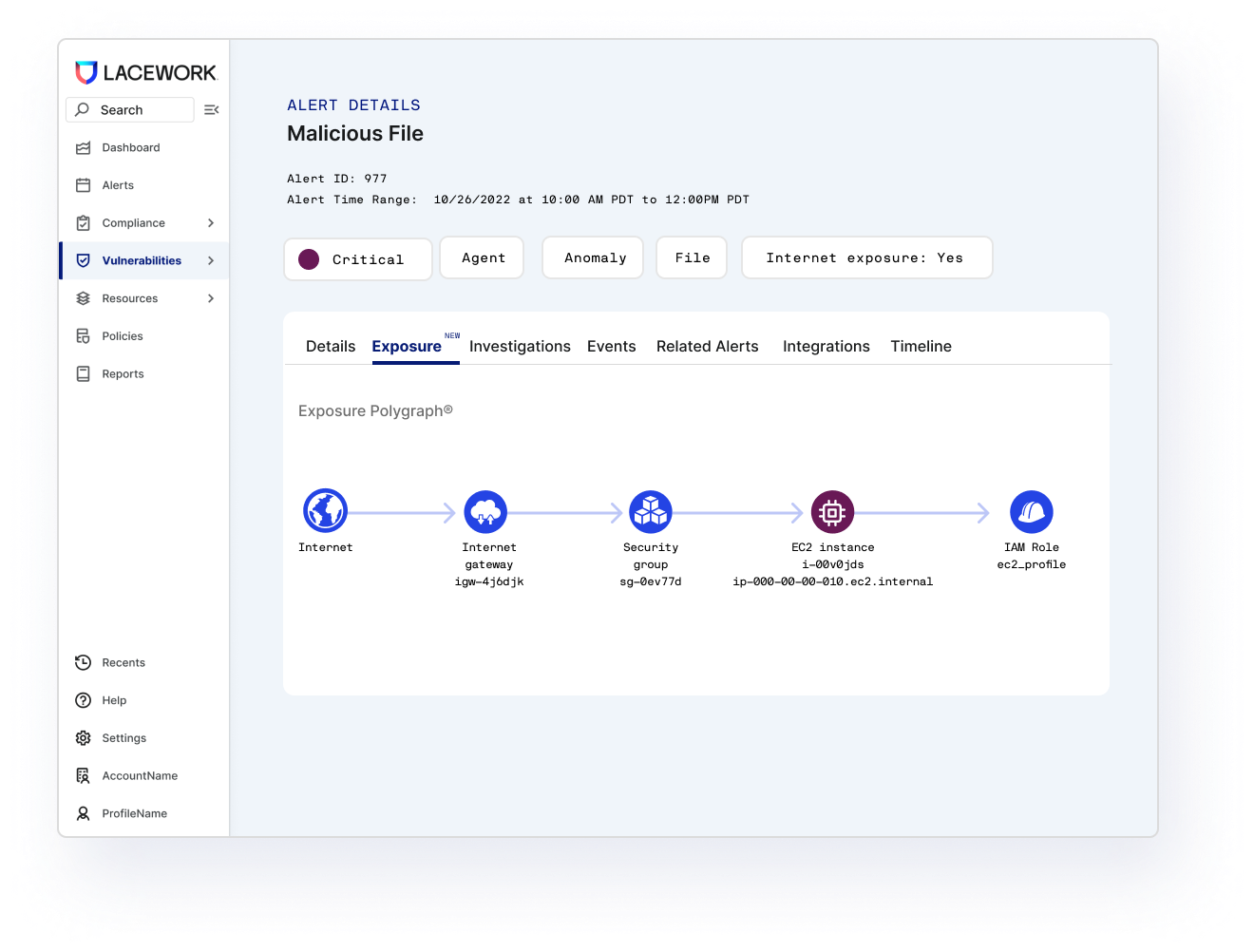
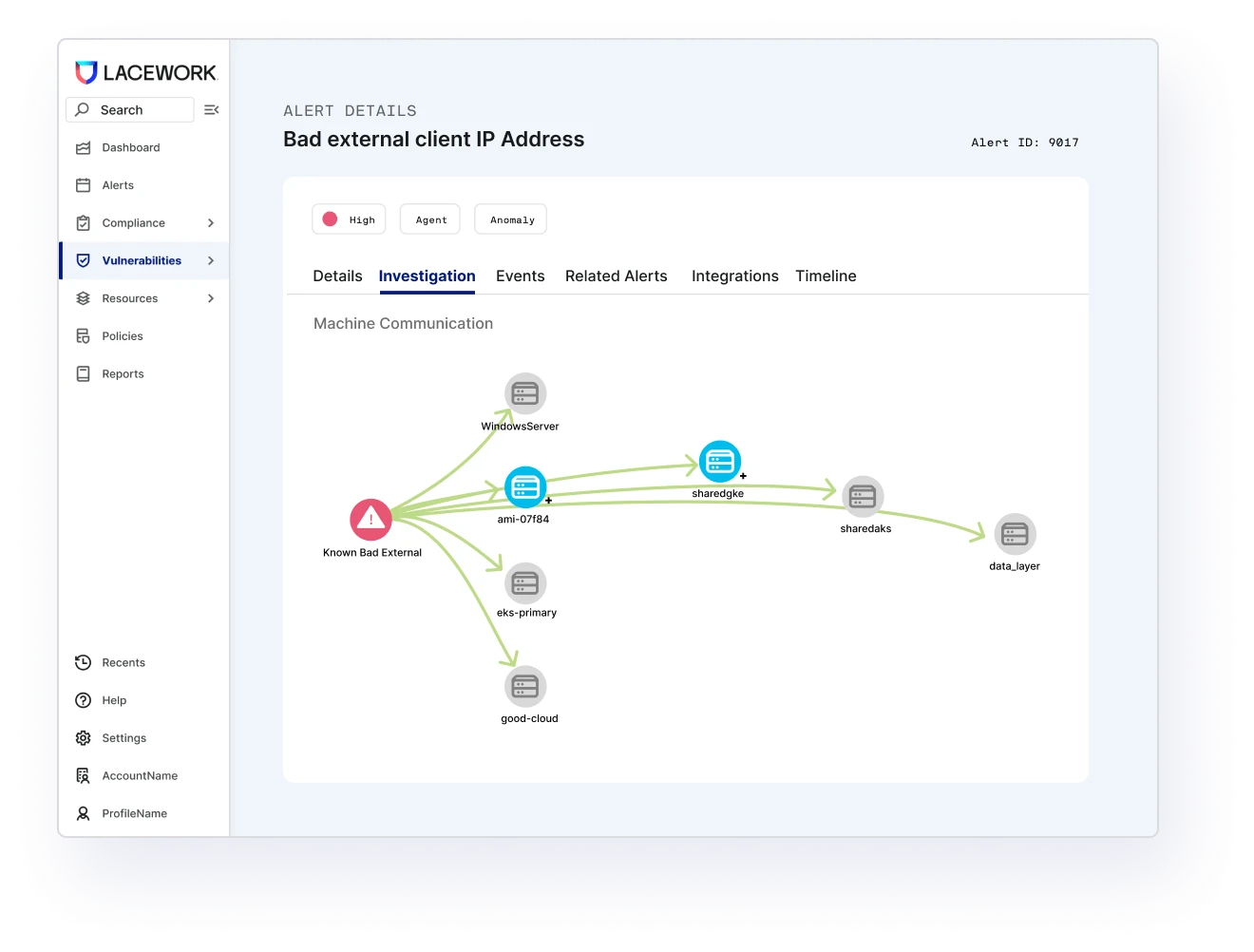
Uncover cloud account compromise
Our patented Polygraph® technology continuously learns your normal to root out suspicious and unusual behavior. Data-driven monitoring reveals compromise and the resulting blast radius. Rich context helps you quickly understand what happened, how, and where to fix it. Our patented approach not only automates threat detection, but can also significantly reduce your SIEM ingest costs too.
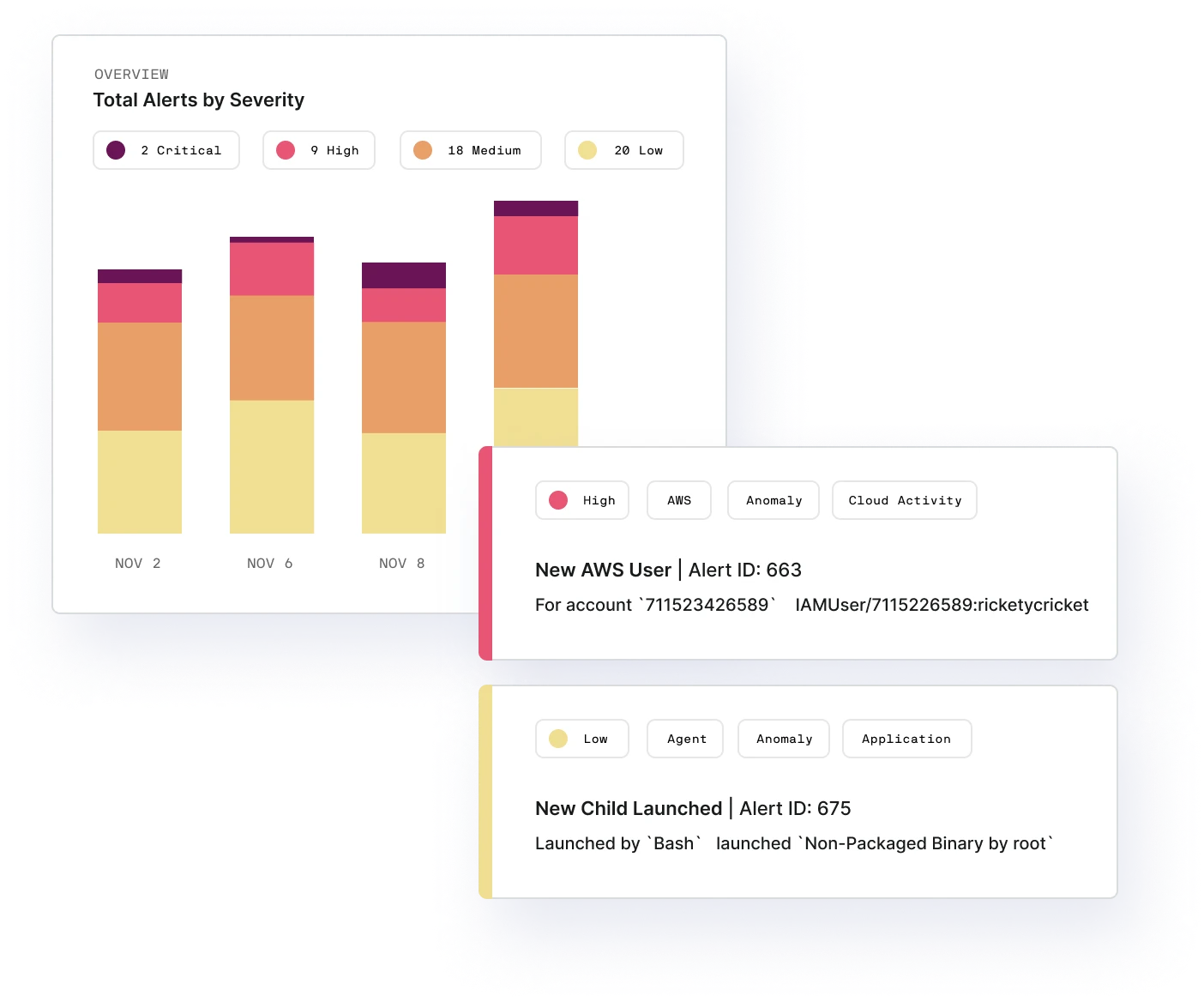
Find threats known and unknown
Continuously protect critical applications and environments with our workload and container security agent. Find new risks lurking in production and understand changes in behavior. Our data-driven approach connects the dots to detect known and unknown threats – even zero day attacks. And do it all automatically without endless rule writing and deep security expertise required.
Fewer tools. Faster outcomes. Better security.
81%
See value in less than 1 week
2 - 5
Average tools replaced
342%
ROI according to Forrester study