Benefit from Active Vulnerability Monitoring at the Host Layer
Ephemeral and immutable compute have changed the economics and velocity of building software, but traditional security approaches have failed to keep up. This includes deciphering which of the millions of known vulnerabilities actually pose a risk to the hundreds of software packages running on thousands of hosts and containers scaling in the cloud. The security of your workloads depends on how well you can find and fix host vulnerabilities across all your cloud environments and workloads deployed on AWS, Azure, and GCP.
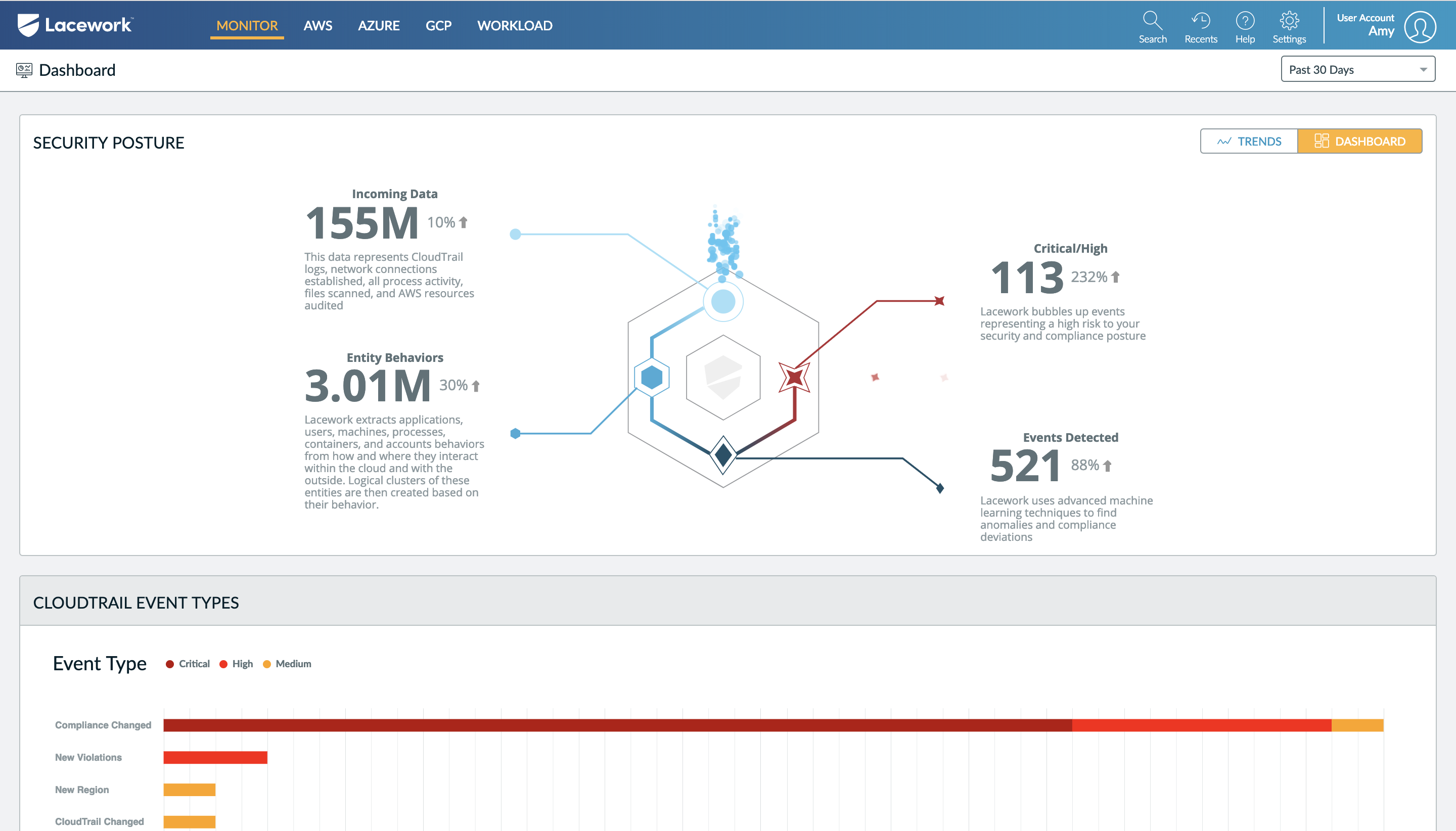
Lacework monitors host vulnerabilities providing detailed context that helps organizations understand their risk posture and address gaps in their cloud environment.
Lacework’s Active Host Vulnerability Monitoring Capabilities Provide:
- Monitoring for Ephemeral Hosts at Scale: Telemetry to distill and focus on vulnerabilities in ephemeral and immutable infrastructure
- A Pre-Flight Check API: Scan a host image (e.g., AWS AMI) for known vulnerabilities before deploying to a live environment
- Scanning for Active Vulnerabilities: Connect known CVEs with active packages on hosts for live visibility to active packages with associated vulnerabilities
- Support for CI/CD and Infrastructure-as-Code Integrations: Tighten the feedback loop and shift security left by integrating the Lacework API into GitHub, GitLab, Jenkins and other workflows
- Reporting Designed to Help Security Teams Focus on What Matters: Shift security right with tailored reports on new active CVEs, and know definitively when a patch has been applied
- An Updated CLI: CLI updates for self-serve vulnerability scanning and data and a new vulnerability dashboard
Get High-Fidelity Host Vulnerability Alerts
Lacework’s console raises alerts when vulnerabilities are detected during a host assessment. At launch, the Lacework platform supports alerting to any routing channel like Slack, Jira, Pager Duty, and others of the following scenarios:
- A new software vulnerability within monitored hosts for a defined severity level
- A known software vulnerability within monitored hosts for a defined severity level
- A software vulnerability severity change within monitored hosts
- A software vulnerability patch status change within monitored hosts
Receive Actionable, Easy to Navigate Information About Each Vulnerability
- Conduct pre-flight vulnerability checks on your containers and workloads prior to shipping to production
- Review host vulnerabilities with rich context and take action
- Triage and prioritize fixes with information at your fingertips
- Quickly find new vulnerabilities when they appear
Take Advantage of Comprehensive Data Collection
- Host vulnerability data capture is continuous and automatic
- Record available telemetry from relevant cloud processes
- Support compliance efforts with comprehensive metrics
- Integrate Lacework data with technology partners like DataDog, New Relic, and Snowflake
Receive Accurate Alerts with Rich Context
- Activities and events organized into behaviors provide visibility and context
- Aggregation, risk scoring, and customization all work to minimize alert noise while improving fidelity
- Links and additional information make it easy to get to the bottom of each alert with just a few clicks
Conduct Comprehensive Vulnerability Checks
Making full use of the National Vulnerability Database as well as vulnerabilities uncovered by our own research team, Lacework Labs, the Lacework platform now checks every package against more than two million CVEs. By checking every package against the full library of CVEs and known threats, we not only catch packages with vulnerabilities that were just released, but we can also even detect package vulnerabilities that were released many years ago. Combined with Lacework’s ability to use UEBA to track and alert on anomalies, this new capability means that Lacework can provide unparalleled detection for known and unknown threats.
Know the Difference Between Vulnerability and Being Vulnerable
A vulnerability is a weakness in a software system. Organizations become vulnerable when a vulnerability is exploited in an attack that leverages that vulnerability. Modern cloud security is about balancing risk and reward. While having a vulnerability isn’t great, the risk factor increases significantly once the vulnerability is an active exploit in the wild and the vulnerability is in production.
Experts estimate that 24% of organizations have hosts missing high-severity patches in the public cloud, and the problem could be much worse for larger enterprises. While assessing a recent environment, Lacework discovered 51,000 vulnerabilities present across a multi-cloud infrastructure. At the current patch rate for most environments, it would take a significant amount of time to patch all those vulnerabilities (average time to patch in the cloud is more than 30 days).
Using Lacework’s new host vulnerability monitoring scans, a security team leader was able to quickly determine that those vulnerabilities were related to 2,800 actual hosts. And of those hosts, those vulnerabilities could be traced to 78 images that needed to be repaired. With the new scope of work reduced to a manageable level, the security and DevOps teams were able to address the gaps in less than a week.
What Our Customers Say
- “My argument with InfoSec is always the same. If I take Lacework out, what’s the alternative? There isn’t one.”
Matthew Zeier
Wavefront - “Lacework Polygraph, within minutes of the attack occurring, was able to detect something that the other ones were not. It outperformed everything we’ve been doing.”
Mario Duarte
Snowflake Computing - “I’m extremely happy with Lacework. I sleep better at night knowing we have full visibility into our cloud operations. It was the one tool that checked all my security boxes.”
Devin Ertel
Guidebook - “Lacework offers us speed and offers us the ability to focus on what we do in terms of building a great product that’s secure. I would definitely recommend it to other IT professionals or product companies that are building a cloud-based application.”
Ian O’Brien
Arista Networks





