The Power of Polygraph® for Configuration Compliance
Lacework’s foundation is Polygraph, a deep temporal baseline built from collecting high fidelity machine,process, and user interactions over a period of time. The Polygraph is used to detect anomalies, generate appropriate alerts, and provide a tool for users to investigate and triage issues.
Fundamentally, Lacework’s Polygraph technology develops a dynamic behavioral and communication model of your services and unique infrastructure. The model understands natural hierarchies for processes, containers, pods, and machines and aggregates them to develop behavioral models. A behavioral model is, in some sense, the essence of how a customer’s infrastructure operates. With this model, Polygraph monitors your infrastructure for activities that fall outside the model. In addition, Polygraph continually updates its models as your data center behavior changes.
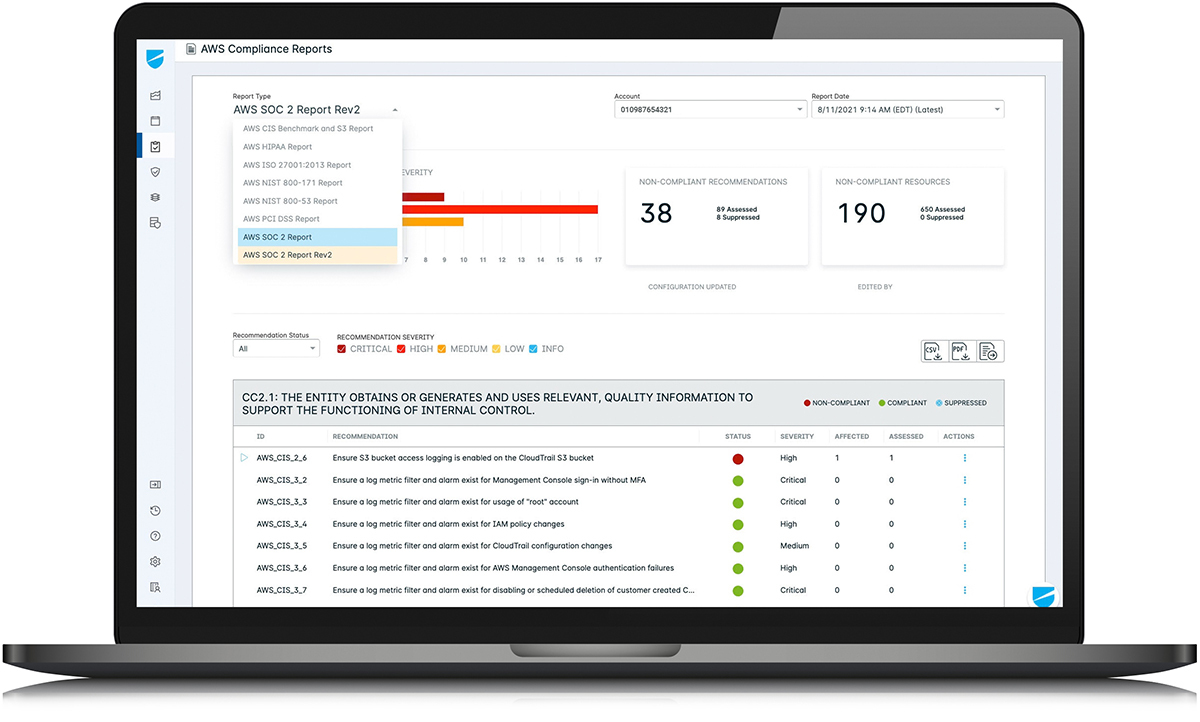
Spot IaaS account configurations that violate compliance and security best practices that could put your company at risk with Lacework’s comprehensive configuration compliance monitoring tools for enterprise DevOps teams.